Cyren experts discovered the Syrk cryptographer, built on the basis of the open-source malware Hidden-Cry, whose source codes were published in the public domain at the end of last year. Syrk ransomware targets cheaters at Fortnite.
Malicious software disguises itself as a game hacking utility and promises to give players an advantage in accurate aiming, knowing the exact location of other players.Reference:
The global gaming phenomenon Fortnite has a huge user base from the worldwide. According to last report, in March it accounted 250 million gamers – and the just-concluded Fortnite World Cup with its $30 million prize pool and an online viewing audience of over two million has certainly only added to its allure.
In fact, instead of the desired aimbot, players download a malware that immediately after launch starts encrypting files on their computers, adding to them the .Syrk extension.
The malware also tries to distinguish between Windows Defender and User Account Control (UAC) on the infected machine, achieve a constant presence in the system and carefully monitors processes that can lead to its termination (task manager, Procmon64 and ProcessHacker).
In addition, the ransomware is trying to infect USB drives connected to the system for further distribution.
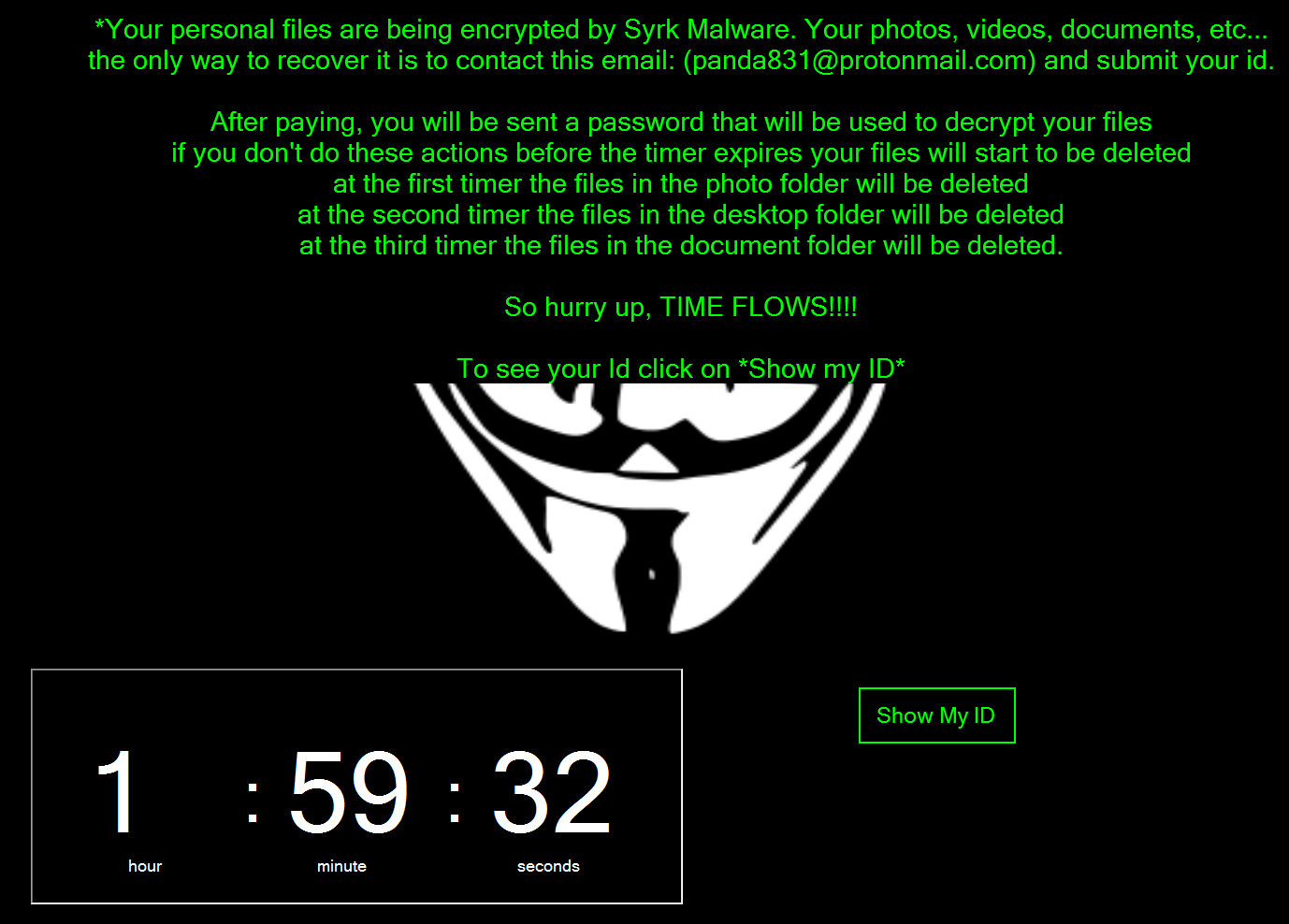
Ransomware screen
Having finished encryption, the ransomware tries to force its victims to pay the ransom as soon as possible.
“One principle feature of the Hidden-Cry ransomware is that, as seen in the instructions shown, it creates the sense of urgency in the victim by deleting files every two hours”, — reported Cyren specialists.
However, Cyren researchers believe that recovering deleted files and decrypting other data is possible without paying attackers.
Researchers immediately found two possible methods of decrypting the data, since the necessary files are present on the infected computers themselves. One of them is dh35s3h8d69s3b1k.exe, a Hidden-Cry decryption tool built into the original malware. Extracting and executing this file will create the PowerShell script needed to decrypt the information.
Read also: Trojan Saefko compiles a victim’s profile and can spread via USB devices
In addition, the ransomware stores in the system files containing the ID and password necessary for decrypting the files. These are the -i + .txt, -pw + .txt and + dp-.txt files stored in C:\Users\Default\AppData\Local\Microsoft.
Given the size of the global pool of players and the obvious motivation for developing their game, it is not surprising that cybercriminals target Fortnite users. Researchers believe that gamers should wait for new attacks.

